Cribl Peers Into the Data Currents. Here’s What It Found

(Image source: Cribl)
IT observability firm Cribl today took the wraps off “Navigating the data current,” a new report that digs into details of its customers’ data operations from IT and security perspectives. Among the noteworthy trends highlighted by Cribl are the growth of data sources, the popularity of specific cloud destinations, and what’s going on with the SIEM market.
Before we get into the report, it’s important to be aware of Cribl’s position in the IT observability market. The company, which was founded six years ago, serves as a sort of independent broker for fast-moving observability data, including event logs, metrics, and traces. The company’s goal: tamp down the soaring costs of IT observability, while keeping data flows and data fidelity high.
Here’s how Cribl works: Instead of sending raw observability data (logs, metrics, and traces) from its source into a security information and event management (SIEM) tool like Splunk or other security or IT observability tool, the data is first sent into Cribl Stream, which strips out the unnecessary bits that drives up the data analysis costs. It also mixes the data with other relevant sources and stores the data in low-cost storage for later playback and retrieval.
Running Cribl Stream in the cloud gives Cribl a great perch to see how customers are building their IT observability stacks, including what data sources they’re using and, perhaps more important, what tools they’re using, such as SIEM, endpoint detection and response (EDR), extended detection and response (XDR), SecOps, and AIOps, among others. It shared those observations with today’s inaugural “Navigating the data current” report, which you can access here.
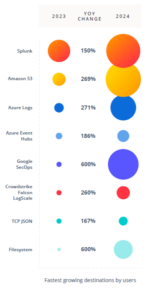
Some of the findings aren’t surprising, such as that the number of data sources is increasing. Cribl found the number went up 32% from last year. The company also found that 18% of Cribl.Cloud customers are consuming data from 10 or more data sources. The top sources include the data collectors associated with Spunk, REST end points, Windows Event Logs, and Amazon S3, among other sources.
Splunk and Amazon S3 also topped the list of the most popular destinations, which isn’t surprising considering how Cribl inserts itself into the data pipeline for IT observability (one stream’s source is another stream’s destination). Other popular destinations for observability data in the Cribl.Cloud ecosystem are Azure Logs, Azure Event Hubs, and Google SecOps, among others.
On the SIEM front, Cribl says the fastest growing cloud-based destination is Microsoft Sentinel, which runs in the Azure cloud. Cribl says its customers’ Sentinel data loads increased whopping 2,000% year over year. Why is this product growing? Cribl says: “Microsoft Sentinel is dominating many conversations with security teams and CISOs owing to Microsoft’s bundling of the product in its popular E5 premium subscription tier.”
While customers would prefer to have a single cloud, Cribl says customers increasingly are adopting multiple SIEM products because of their “perennial disappointment” in their chosen product. The company says there has been a 73% increase from 2023 to 2024 in the number of customers using multiple SIEMs.
“Splunk, the clear market leader in SIEM, is under fire as teams most frequently send data to Google SecOps and CrowdStrike in addition to Splunk,” Cribl writes in the report. “This is understandable as there is significant uncertainty in the market after Cisco’s acquisition of Splunk.”
It’s worth nothing that there is also significant uncertainty in CrowdStrike’s popular offerings following the historic Internet outage of July 19, which was traced to a malformed security update for Windows systems issued by CrowdStrike. The outage was exacerbated by the heavy reliance that Microsoft placed on CrowdStrike to protect its systems in Azure, which also experienced heavy outages.
In any event, the time for SIEM at the pointy-est end of the security spear might be up, as the market increasingly is shifting from SIEM to XDR, a phrase coined by Palo Alto Networks CTO Nir Zuk back in 2018. XDR products basically are an extension of endpoint- (or EDR) focused security tools, and have the advantage of collecting and processing relevant security data from everything under the IT sun, from servers and SANs to network gear and Windows desktops.
Whether customers are moving from SIEM to SIEM or SIEM to XDR, Cribl’s value as the observability middleman remains the same.
“Migrating to a new SIEM means taking on some risk because, without Cribl, it’s a one-way door. Once you walk through it, you can’t go back,” the company says in its report. “Cribl turns that migration into a two-way door. You can send data to different SIEMs in the format they expect with no loss of fidelity, and without weakening your security posture.”
Related Items:
The White Label Powering IBM’s New Cloud Logs Solution
Cribl Seeks Control of Observability Data Run Amok
Companies Drowning in Observability Data, Dynatrace Says